Trusted Computing
2020 Design of Terminal Security Access Scheme based on Trusted Computing in Ubiquitous Electric Internet of Things
https://ieeexplore.ieee.org/document/9339022
基于电气物联网中可信计算的终端安全访问方案设计
keywords: ubiquitous electric internet of things,trusted computing,terminal access,secure access
Guodong Wang proposed a dual-system design scheme for terminal active immunity based on trusted computing. In this scheme, the terminal node in UEIoT is composed of two parts: computing part and trusted protection part. The computing component and the trusted protection component are logically independent of each other, forming a trusted computing active immune dual-system structure with both computing and protection functions. The Trusted Network Connection extends the trusted state of the terminal to the network, thus providing a solution for terminal secure access in the UEIoT.
They proposed a dual-system scheme for terminal active immunity based on trusted computing. In this scheme, the terminal node is composed of two parts: computing part and trusted protection part. The trusted protection part relies on the cryptographic services provided by TCM and the active measurement and control functions provided by TPCM to realize the chain of trust to be passed forward in the form of active adjudication. It can overcome the defects caused by the mounting method and passive invocation of TPM component in the traditional TCG and form a dual-system active security protection architecture with the existing security system in the host computing system.
这篇文章很符合预期,既有可信计算,又涉及终端安全。
作者希望构建具有计算和保护功能的可信计算-主动免疫双系统结构。
2020 Security of Edge Computing Based on Trusted Computing
https://ieeexplore.ieee.org/document/9265904/metrics#metrics
基于可信计算的边缘计算安全
This paper mainly analyzes the threats faced by edge computing and the current security architecture, and puts forward a protection mechanism based on trust and cooperates with blockchain technology to improve the security and reliability of edge computing. If a separate security framework for edge computing can be proposed according to this article, it will play a role in the healthy development of edge computing.
这篇文章实际上主要在将边缘计算,以及在区块链中的应用。这并不是主动防御和系统安全的主要关注点
文中还提出与基于病毒防护、防火墙和入侵检测的传统终端安全解决方案相比,可信计算的核心理念是嵌入计算机平台(如 TPM)的嵌入式微机系统。它可以解决许多以前无法解决的问题。TPM 实际上在计算机系统中增加了一个受信任的第三方,并且系统可以通过测量和约束系统来被受信任的第三方信任。
Bin Ma 等人认为应该分层考虑安全系统的设计,不同层次之间有不同的属性和安全要求。
2021 SDSBT: A Secure Multi-party Data Sharing Platform Based on Blockchain and TEE
https://link.springer.com/chapter/10.1007/978-3-030-73671-2_17
基于区块链和TEE的安全多方数据共享平台
This paper proposes SDSBT, a multi-party data sharing platform based on blockchain and the trusted execution environment (TEE), which effectively and securely realizes the data sharing among multiple parties. SDSBT achieves the properties including privacy-preserving, identity authentication, application security, and accountability.
提出了基于区块链和可信执行环境(TEE)的多方数据共享平台,实现了隐私保护、身份验证、应用程序安全和责任等特性。作者也做了分成的设计,不过他们的设计与Bin Ma的有所区别:合同层、数据传输层、数据操作层、数据共享层和存储层。
2021 An attack-immune trusted architecture for supervisory aircraft hardware
https://www.sciencedirect.com/science/article/pii/S1000936121000637?via%3Dihub
作者结合免疫的概念,提出一种用于监控飞机硬件的攻击免疫可信体系结构
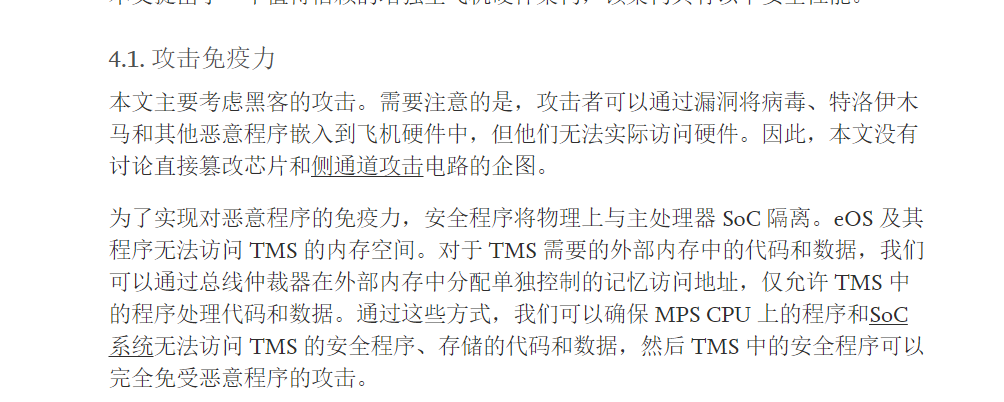
针对飞机硬件的安全问题,提出了一种基于安全片上系统。该体系结构具有攻击免疫性和可信任性,能够在不受干扰的情况下支持可信托管应用和动态完整性度量。在该文的方案中,系统的安全程序将物理上与主处理器 SoC 隔离。
Intelligent security
2021 Intelligent immunity based security defense system for multi-access edge computing network
https://ieeexplore.ieee.org/document/9339833/keywords#keywords
基于智能免疫的多访问边缘计算网络安全防御系统
In this paper, the security problem for the multi-access edge computing (MEC) network is researched, and an intelligent immunity-based security defense system is proposed to identify the unauthorized mobile users and to protect the security of whole system. In the proposed security defense system, the security is protected by the intelligent immunity through three functions, identification function, learning function, and regulation function, respectively. Meanwhile, a three process-based intelligent algorithm is proposed for the intelligent immunity system. Numerical simulations are given to prove the effeteness of the proposed approach.
本文研究了多接入边缘计算(MEC)网络的安全问题,提出了智能免疫安全防御系统,以识别未经授权的移动用户,保护整个系统的安全。在拟议的安全防御系统中,安全性分别通过识别功能、学习功能和调节功能三个功能受到智能免疫的保护。同时,提出了智能免疫系统的三种基于过程的智能算法。进行数字模拟以证明拟议方法的有效性。
2019 Real-Time Early Warning of Network Security Threats Based on Improved Ant Colony Algorithm
https://ieeexplore.ieee.org/document/9017019
基于改进的蚂蚁群落算法的网络安全威胁实时预警
Firstly, the network security threat perception algorithm is optimized based on the principle of neural network, and the network security threat detection process is standardized according to the optimized algorithm. Finally, the real-time early warning of network security threats is realized. Finally, the experiment proves that the network security threat real-time warning based on the improved ant colony algorithm has better security and stability than the traditional warning methods, and fully meets the research requirements.
基于神经网络原理优化网络安全威胁感知算法,根据优化算法对网络安全威胁检测过程进行标准化。最后,实现了网络安全威胁的实时预警。最后,实验证明,基于改进的蚂蚁群落算法的网络安全威胁实时预警比传统的预警方法具有更好的安全性和稳定性,完全符合研究要求。
2020 Toward Proactive, Adaptive Defense: A Survey on Moving Target Defense
https://ieeexplore.ieee.org/document/8949517
主动、自适应防御:移动目标防御调查
综述性文章。讨论了 MTD(移动目标防御) 在入侵预防机制和检测潜在攻击者方面的作用,讨论了本工作所涵盖的现有 MTD 方法的局限性,并提出了未来在MTD研究领域的研究方向。
2019 Artificial Intelligence based Network Intrusion Detection with Hyper-Parameter Optimization Tuning on the Realistic Cyber Dataset CSE-CIC-IDS2018 using Cloud Computing
https://ieeexplore.ieee.org/document/8698029
基于人工智能的网络入侵检测
The proposed system can be extended to detect all other remaining classes of attacks in this realistic dataset which includes all real-time and existing attacks.
所提出的系统可以扩展到检测这个真实数据集中所有其他类型的攻击,其中包括所有实时和现有的攻击。此人工智能Scikit学习框架优化中使用的框架基于中央处理单元,而不是图形处理单元,优化可能会被其他此类框架(如谷歌的开源Tensor Flow)有力地调整。当我们遇到熊猫来处理更大的数据(100千兆字节到多TB)时,性能问题是一个常见的任务,但是Spark是一个用于大数据处理的开源Apache框架,它可以处理集群计算机上从100千兆字节到多TB的海量数据集的并行计算。
Automatic computing
知网找到的有关自主计算的文献基本很久远
2021 A review on architecture and models for autonomic software systems
https://link.springer.com/article/10.1007/s11227-020-03268-0
(这篇文章引用了之前LNCS文章的一篇经典自动计算的文章 Towards Enabling Autonomic Computing in IoT Ecosystem https://ieeexplore.ieee.org/document/8890456,引用该文的文章列表可以参考 https://scholar.google.com/scholar?cites=14309675548026047319&as_sdt=2005&sciodt=0,5&hl=zh-CN)
自主软件系统架构和模型回顾
该文对自主决策概念及其在入侵检测、基于云的数据安全、无线传感器网络、物联网、大数据等诸多无法实时管理的领域的重要性提供了深入的见解。并且讨论了不同研究人员在研究估计系统自主性水平时建议并实施的一些解决方案。这些解决方案将有助于根据每个应用程序中实现的自主特征比较不同的自主应用。
2021 Autonomic Resource Management in a Cloud-Based Infrastructure Environment
https://link.springer.com/chapter/10.1007/978-3-030-71756-8_18
基于云的基础设施环境中的自主资源管理
该文概述了自主云计算环境的方法和机制。自主计算完全执行动态配置资源的方式,以便实时重新配置资源。还为领域研究人员分析了自主资源管理的最高特征提供了一条直截了当的方法,并有助于研究学者识别和描述未来研究角度与环境相对应的应用的主要技术。
2021 Autonomic Computing on Cloud Computing Using Architecture Adoption Models: An Empirical Review
https://link.springer.com/chapter/10.1007/978-3-030-71756-8_11
使用架构采用模型的云计算自主计算:经验回顾
This paper presents a brief review on autonomic self-management attributes and capabilities of machine additives, describes autonomic computing architectures, autonomic adoption modes and requirements, and examines its properties over cloud computing.
该文主要描述了自主计算体系结构、自主采用模式和需求,并分析了其在云计算上的特性。
2021 The Architecture of Autonomic Cloud Resource Management
https://link.springer.com/chapter/10.1007/978-3-030-71756-8_14
自主云资源管理架构
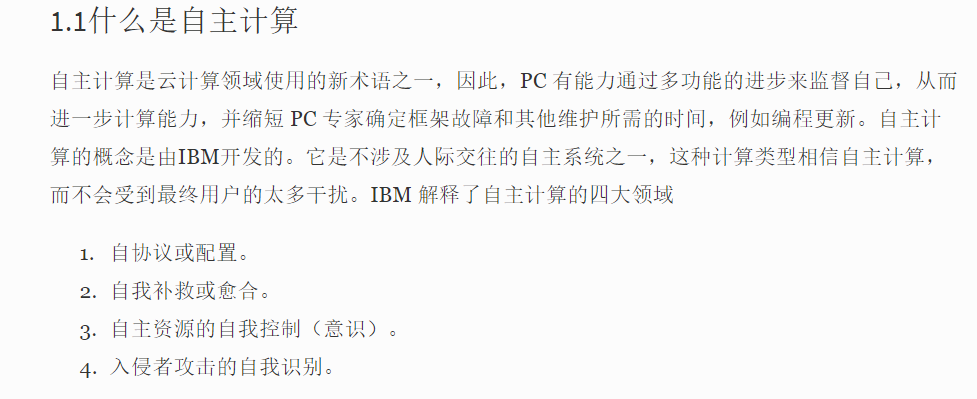
该文提到 IBM 解释的四大领域,其中入侵检测是我们关注的重点,但没有更详细的有关自主计算的文章讲述入侵检测了。