Re
pypy
- 题目所给的时Python字节码,如下
1 | 4 0 LOAD_GLOBAL 0 (input) |
- 将字节码翻译为Python代码,参考
1 | raw_flag = input('give me your flag:\n') |
- 解密代码为
1 | res = '30466633346f59213b4139794520572b45514d61583151576638643a' |
- 结果为
G00dj0&_H3r3-I$Y@Ur_$L@G!~!~
Crypto
まひと
- 下载文件并打开,时morse电码,解码得到
1 | 86/109/108/110/90/87/53/108/99/109/85/116/84/71/108/114/97/84/112/57/86/109/116/116/100/107/112/105/73/84/70/89/100/69/70/52/90/83/70/111/99/69/48/120/101/48/48/114/79/88/104/120/101/110/74/85/84/86/57/79/97/110/53/106/85/109/99/48/101/65/61/61 |
1 | VmlnZW5lcmUtTGlraTp9VmttdkpiITFYdEF4ZSFocE0xe00rOXhxenJUTV9Oan5jUmc0eA== |
1 | Vigenere-Liki:}VkmvJb!1XtAxe!hpM1{M+9xqzrTM_Nj~cRg4x |
- 维吉尼亚加密,且密钥为Liki,解密
1 | }KccnYt!1NlPpu!zeE1{C+9pfrhLB_Fz~uGy4n |
- 因为明文中是包含hgame的,因此必有移位,遍历以下移位后结果中包含hgame的
1 | def caesar(c, n): |
结果为移位13时包含,字符串为}XppaLg!1AyCch!mrR1{P+9cseuYO_Sm~hTl4a
- 根据括号的位置可以判断还有一层栅栏密码,尝试发现每组字数6,得到
}!!Pu~X1m+YhpAr9OTpyRc_laC1sS4Lc{emagh字符串反转一下得到flaghgame{cL4Ss1Cal_cRypTO9rAphY+m1X~uP!!}
WhitegiveRSA
确实白给
- 先大数分解得到p和q分别为857504083339712752489993810777和1029224947942998075080348647219
- python代码如下
1 | import gmpy2 |
MISC
Week-1
不起眼压缩包的养成的方法
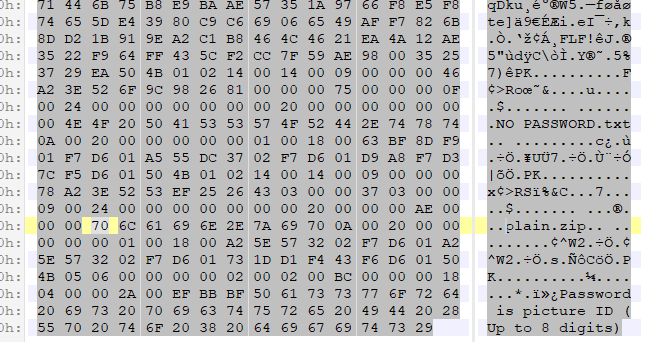
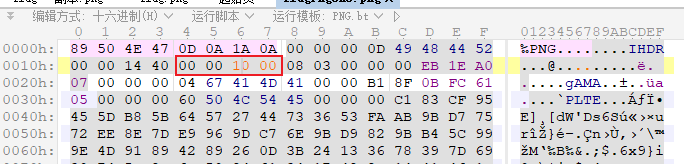
- 下载得到一个jpg文件,用010Editor打开,发现末尾有
- 因此推测jpg中包含zip文件,且口令为8位数字
- 用
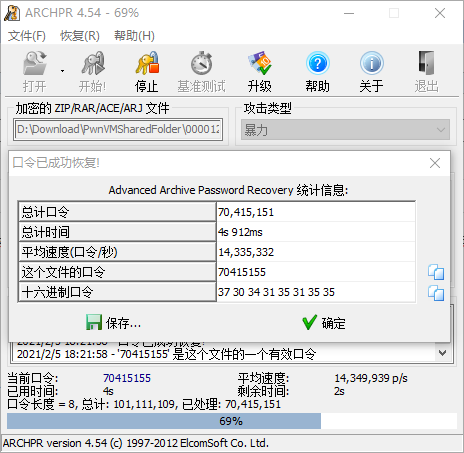
foremost分离出zip文件,并使用Advanced Archive Password Recovery暴力破解,得到口令为70415155 - 成功解压缩,得到两个文件
- 发现plain.zip中还有个NO PASSWORD.txt且没有更多的提示,因此应该是利用这个文本文件进行已知明文攻击,参考
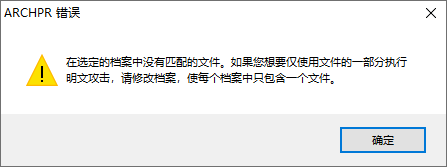
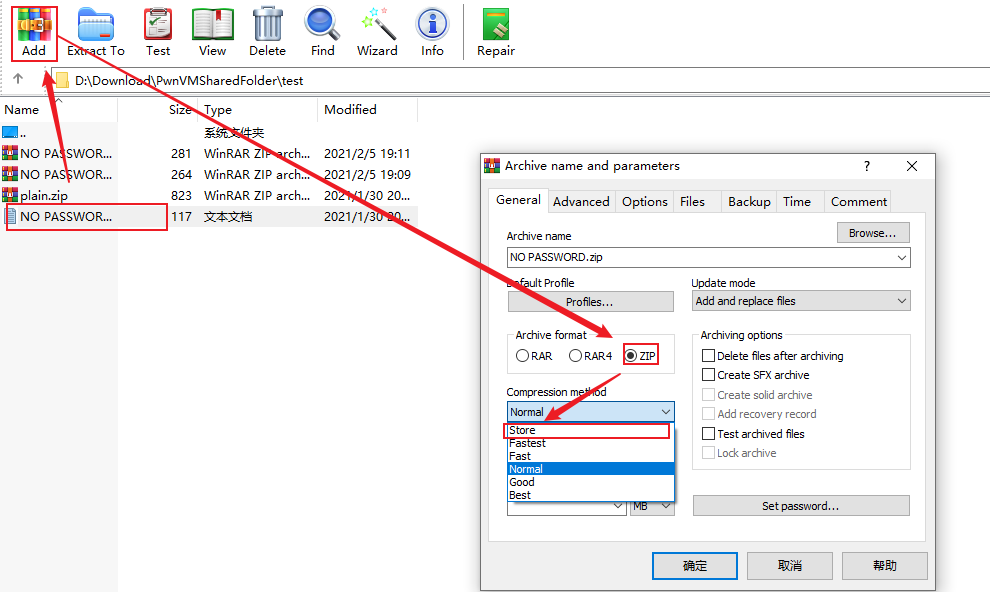
- 在ARCHPR中添加待解密的文件和我们自己压缩的文件,最初在此遇到了报错
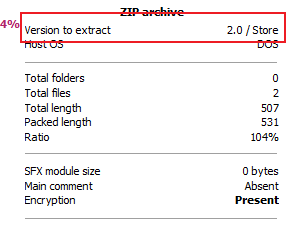
- 因此换成winRAR进行压缩,在压缩前查看了已有的待破解压缩包的属性有
- 因此将NO PASSWORD.txt以同样的方式进行压缩
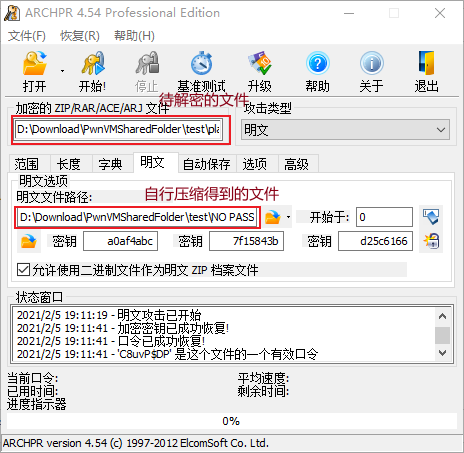
- 现在可以成功开始
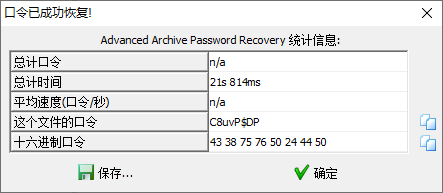
- 最终得到口令为
C8uvP$DP - 解压plain.zip得到其中的flag.zip,由于没有更多的提示,所以用010Editor查看以下,得到以下信息
- 将这段值复制出来转成ASCII即可得到flag为
hgame{2IP_is_Usefu1_and_Me9umi_i5_W0r1d}
Galaxy
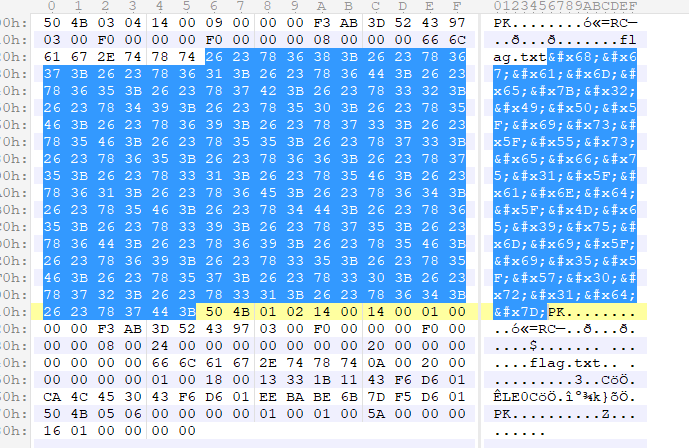
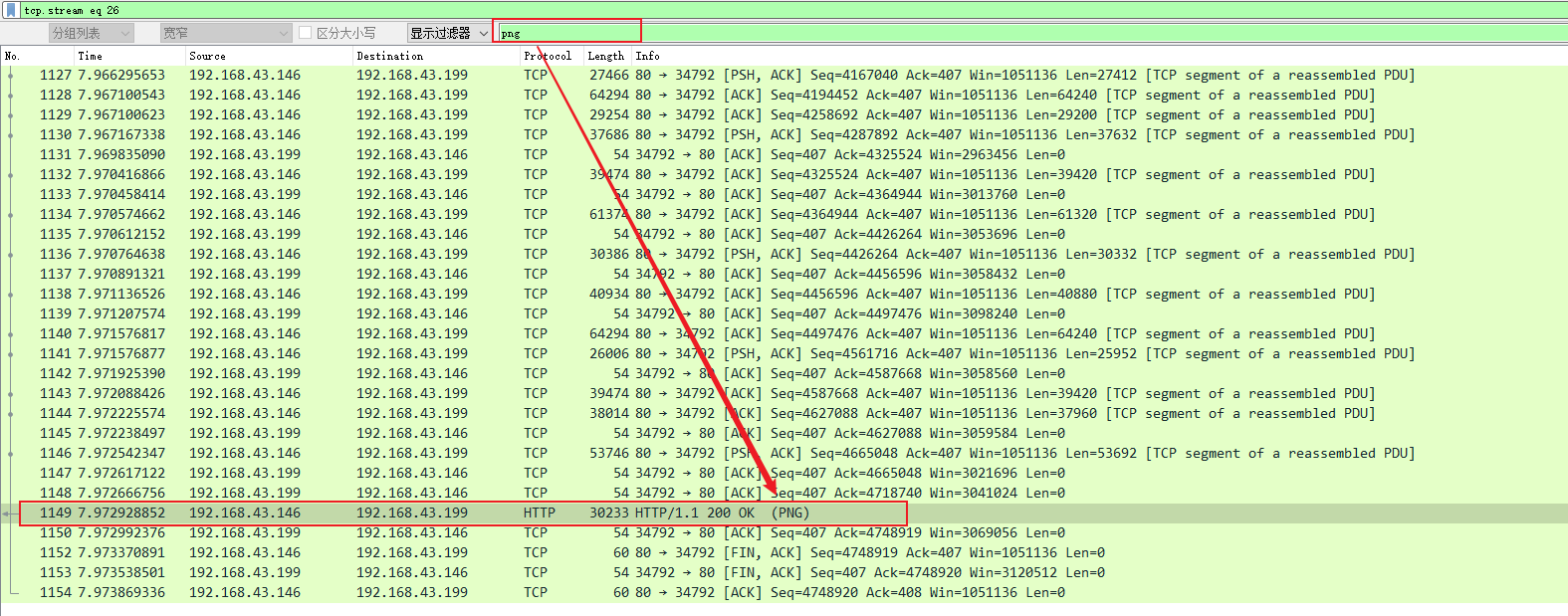
- 下载pcapng文件,拖到wireshark看下,根据提示有一张星空壁纸,所以先搜索有无png
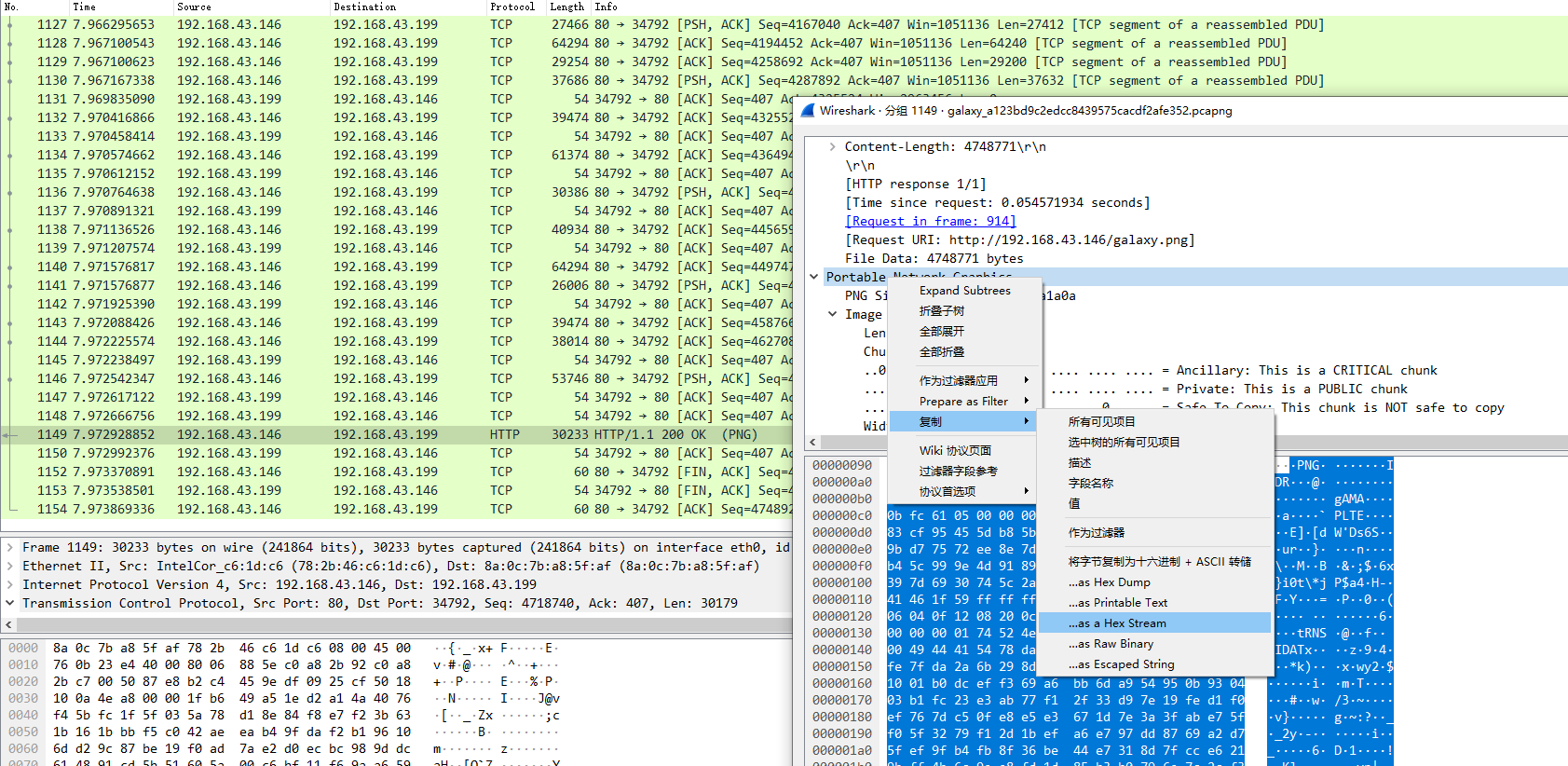
- 双击这条,然后找到PNG文件流所在位置,复制hex流
- 用Python将其转为文件
1 | import binascii |
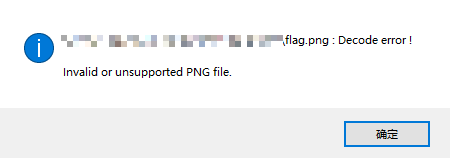
打开得到的png文件却提示
用010Editor打开提示CRC校验错误,看一下图片宽高,因此可能是高度有错,通过CRC爆破即可,这里参考以前的一篇博客,只需改下图片名即可
1 | import struct |
- 输出结果1000,因此将高度改为1000即可看到flag
1 | hgame{Wh4t_A_W0nderfu1_Wa11paper} |
Word RE:MASTER
- 解压缩发现两个文件,maimai.docx需要口令,因此推测first中有关键信息
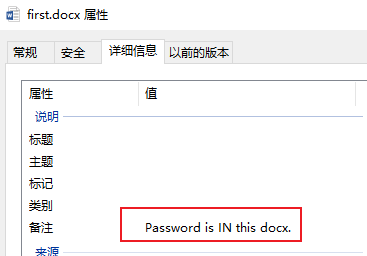
查看文件属性也可以发现提示 - binwalk查看
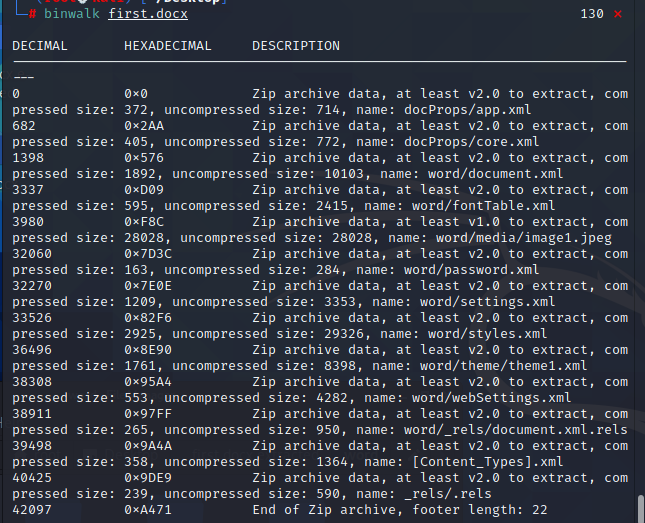
binwalk -e first.docx分离文件,发现有个password.xml- 打开后得到
1 | +++++ +++[- >++++ ++++< ]>+++ +.<++ +[->+ ++<]> ++.<+ ++[-> +++<] >+.<+ ++[-> ---<] >-.++ ++++. <+++[ ->--- <]>-. +++.+ .++++ ++++. <+++[ ->--- <]>-- ----. +.--- --..+ .++++ +++++ .<+++ [->-- -<]>- ----- .< |
Brainfuck解密,得到
DOYOUKNOWHIDDEN?用其成功打开maimai.docx
请教大佬,发现是snow隐写参考
将docx导出txt文件
SNOW.EXE -C maimai.txt
1 | hgame{Cha11en9e_Whit3_P4ND0R4_P4R4D0XXX} |